Do you want to know how to use the 4 most accurate user identification tools? If so, keep reading!
You may have observed that it is getting harder to keep your users interested if you have a website or app. This is because there are many websites and applications that are comparable to yours. User identification is becoming increasingly important in today’s world because it enables you to target particular users according to their preferences, interests, and actions.
Furthermore, user identification can help you develop better marketing strategies; in order to reach your target audience and keep them engaged with your website or app. So, if you’re planning on developing a website or an app; or even if you’re just starting a marketing campaign; it is important to know how to identify users. There are numerous ways of doing so, but the best one we recommend is using a User Identification Verification API.

Engineers don’t typically start from scratch when writing code. It enables programmers to reuse complex, repetitive procedures with less code. The rate at which developers are able to create applications is essential to the development of applications nowadays. When they have to create more code from scratch, engineers are now more productive than before. Every time they produce a new program, they do not need to reinvent the wheel. They might instead concentrate on their applications’ distinctive suggestions while removing any asset functions from them.
Username Availability Checker API
The Username Availability Checker API should be used by anyone utilizing social media management software, whether they are an individual, a business, or both. You may save time, effort, and frustration by developing your ability to make informed decisions. With the use of this API, you may establish a consistent username across all platforms, eliminating the need for guesswork or settling for worse options.
Enter the username to verify together with the selected social media as a parameter with a name like “social” for the websites that this API supports to get it validated. As an illustration, the result in this instance demonstrated that the “instagram” account was a fraud:
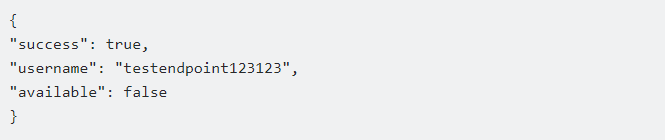
You must register before using this Username Availability Checker API. Click “START FREE TRIAL” to begin the trial. You may then start executing API queries after that. You can call the API by choosing “test endpoint” and entering the username you want to verify. The response will provide all the data you need for the username. Now that you know how to utilize it, you can use it for development!
Alternatively, you might try these options:
OAuth 2.0

With the help of the OAuth 2.0 protocol, users can access APIs without revealing their login information. It is frequently used for authentication in desktop, mobile, and web applications. Users of APIs can authenticate their identity without having to give the API their username and password each time they make a request thanks to the essential “token” idea of OAuth 2.0.
API clients use authorization credentials (such as a code or password) to obtain access tokens. API providers use scopes to define API access privileges (like read and write). The API resources that adhere to the scopes and authorizations specified in the API can then be accessed by API consumers using the tokens.
OpenID Connect

With the addition of OpenID Connect, the OAuth 2.0 protocol gains a basic identity layer that enables computing clients to obtain basic profile data about end users in an accessible and REST-like way as well as to confirm the identity of an end user based on the authentication carried out by an authorization server.
Using OpenID Connect, a variety of clients, including Web-based, mobile, and JavaScript clients, can ask for and receive information about authenticated sessions and end users. Additional features like session management, finding OpenID Providers, and identity data encryption can be added to the core set of capabilities.
JWT

An open, RFC 7519 industry-standard method for firmly representing claims between two parties is the use of net JSON tokens. JWT can be used to construct, decode, and verify JWT. Auth0 invented JWT, even though it might be used frequently currently.
OpenID Connect provides a discovery method called OpenID Connect Discovery that can be used anywhere an OpenID server publishes its data at a well-known location. A JSON listing of the OpenID/OAuth endpoints, available scopes and claims, public keys used to sign tokens, and other information is returned by this URL. These details will be used by the buyers to create a participation request to the OpenID server. The OpenID Connect Discovery Specification contains a list of the sphere names and values.