Have you developed an API for face liveness checking? Are you trying to find the best monetization system? Do not continue reading since we will expose you to one of the top online marketplaces for topic API. As the world evolves towards digitization, fraudsters are developing more effective strategies to…
Leave a CommentTag: Face Liveness Check API
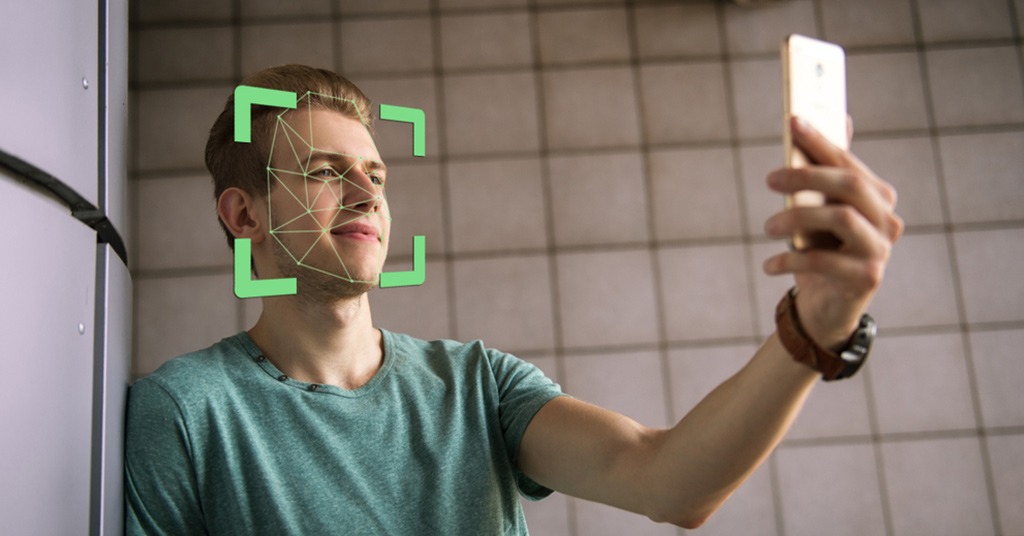
Have you ever wondered how someone can be identified? This process actually incorporates internal facial recognition and identification. Our thoughts examine specific facial characteristics and contrast them with the faces we can recall. This procedure moves quickly and is enjoyable. Additionally, it serves as the basis for a number of…
Leave a CommentHave you developed an API for face liveness checking? Are you trying to find the best monetization system? Do not continue reading since we will expose you to one of the top online marketplaces for topic API. As the world evolves toward digitization, fraudsters are developing more effective strategies to…
Leave a CommentHave you ever wondered how someone can be identified? This process actually incorporates internal facial recognition and identification. Our thoughts examine specific facial characteristics and contrast them with the faces we can recall. This procedure moves quickly and is enjoyable. Additionally, it serves as the basis for a number of…
Leave a CommentSimilar to other biometric verification methods, liveness face recognition is susceptible to biometric spoofing and fabrication. Through the use of fake biometrics, human images, masks, or mannequins, an unauthorized individual may be able to get around the verification process. This sort of authentication bypass technique can be used to compromise…
Leave a CommentHave you ever considered the process of identification? Internal facial recognition and identification are part of this procedure. Our minds analyze particular aspects of the face and compare them to the faces we can remember. The process is enjoyable and moves rapidly. It also forms the foundation for some contemporary…
Leave a CommentFace Liveness Check API is needed to secure biometric authentication systems from fraud. For instance, a fraudster could use a photo, video or mask to attack a facial recognition algorithm and get unauthorized access to accounts or data. This, fraud prevention is the main reason why liveness detection is required…
Leave a CommentAre you interested in learning how facial recognition software works? If so, you’ve come to the right place since we’ll provide you with all the face comparison APIs information you require. In the present, technology has automated practically everything of what a human body is capable of. This includes the…
Leave a CommentDid you ever wonder how someone can be identified? This process actually incorporates internal facial recognition and identification. Our thoughts examine specific facial characteristics and contrast them with the faces we can recall. This procedure moves quickly and is enjoyable. Additionally, it serves as the basis for a number of…
Leave a CommentWould you like to start using an API for the testing phases for your company? In this article we will tell you more about it and which is the best one. The use of face verification technologies has increased recently. a biometric authentication method with use cases in numerous international…
Leave a Comment